Which Access Control Techniques Can Scale To A Cloud Computing Environmen
What Is the Cloud?
Virtually everybody engages in "cloud calculating," but a recent survey revealed that almost people haven't the faintest idea what it is.
Some 29 percent of Americans call up "the cloud" — the thing you access when you lot deject-compute — is an actual cloud, the sky or something else related to the weather, co-ordinate to a nationally representative survey of ane,006 American adults conducted past Wakefield Research.
Other survey respondents defined the cloud as: toilet paper, pillow, smoke, outerspace, net, mysterious network, unreliable, security, sadness, relaxed, overused, oh goody a hacker'south dream, storage, movies, money, retentiveness, dorsum-up, joy, innovation, drugs, heaven and a place to meet. But 16 percent got the definition most right.
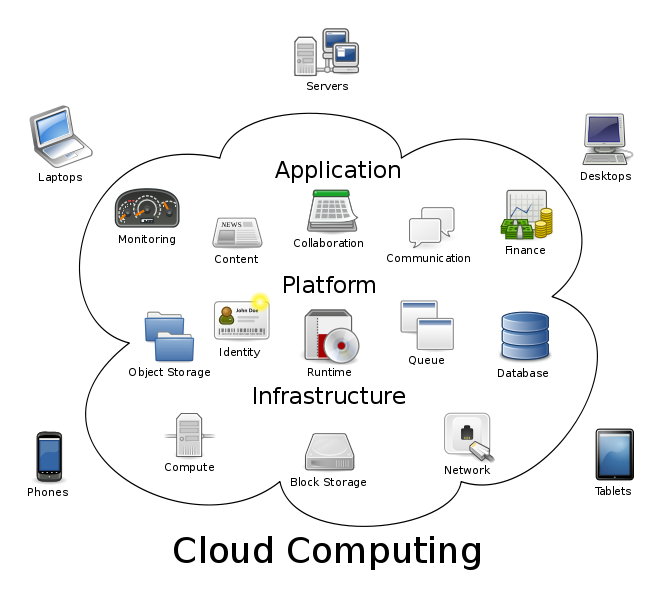
Anytime a person uses a estimator, smartphone or tablet to access data or services stored or hosted elsewhere, they are engaging in cloud computing. For instance, online banking, online shopping, social networking, and remote storage of photos, music or videos are all deject-based services. While deject computing refers to engaging in these online activities, the cloud is sort of an umbrella term for the places where all that remote data is stored, as well as the information itself. [Is it Possible to Retrieve Data When My Computer Fails?]
According to a briefing from the Great britain Office for Library and Information Networking (UKOLN), cloud data, services and infrastructure possess the post-obit characteristics: They are remotely hosted, accessible from anywhere, and they are commodified, meaning you pay for what you use just like with gas and electricity.
Nevertheless a scrap foggy on the cloud? You lot may be overthinking it. As the UKOLN puts it, the cloud is really just a metaphor for the Internet.
Follow Natalie Wolchover on Twitter @nattyover or Life's Petty Mysteries @llmysteries. We're also on Facebook & Google+.
Which Access Control Techniques Can Scale To A Cloud Computing Environmen,
Source: https://www.livescience.com/34183-cloud-computing-definition.html
Posted by: tatecale1985.blogspot.com


0 Response to "Which Access Control Techniques Can Scale To A Cloud Computing Environmen"
Post a Comment